MontyCloud DAY2 Automated Resource Tagging for AWS MAP
Have you signed an agreement to begin migrating to AWS? Or are you a Managed Service Provider (MSP) with an AWS Migration Competency delivering AWS...
4 min read
 Sabrinath Rao
:
Feb 11, 2021 11:37:00 AM
Sabrinath Rao
:
Feb 11, 2021 11:37:00 AM
Cloud security is a moving target because cloud infrastructure is dynamic by nature. Anyone in your team can add or remove resources, scale on demand, or bring resources online for testing. Add to this the fact that applications are deployed across multiple cloud accounts/regions and each service has its own API surface area, configurations, and permissions; soon your environment gets extremely complex. But in dynamic cloud environments, when an asset inventory exercise can become obsolete within moments of completion – how can IT teams keep up?
One of the largest online pharmacies in the United States enables customers to fill their prescriptions online and pickup at one of their 50,000 partner locations. All their applications run on AWS. These applications are built by multiple teams using multiple AWS services. Over time each team created their own accounts, provisioned their own resources and implemented their own policies. This led to unintentional account sprawl. Over 20% in over provisioned resources, abandoned or untagged services, inconsistent governance, and management complexity.
Visibility and context are two pillars that form the foundation of an effective cloud security, compliance and governance and cost management strategy. In this blog I discuss how automation can help IT teams get a real time inventory and contextual visibility into their cloud footprint.
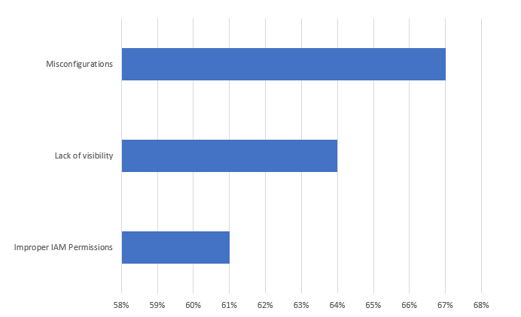
Data Source: https://www.idevnews.com/stories/7376/IDC-Study-Finds-Cloud-Data-Breaches-Impact-80-of-CISOs
Unmanaged, abandoned or orphaned resources are not only a cost burden but also a security threat. In research surveys, CISOs as well as security and compliance administrators consistently rank Lack of Visibility into their environments among their top concerns. An analysis of all the high-profile security breaches since 2015 validate their concerns.
For example, in the most recent breach at SolarWinds, the perpetrators started with the development environment and injected malware into SolarWinds’s software. The perpetrators spent days testing their code.
Frankly, the scenario described here is common. Development teams need a dev/test environment. They spin up a few Amazon EC2 Instances, attach storage and perhaps a database. Finish their testing and move on. Since it is a dev/test environment, there are no governance guardrails or patch management. The developers don’t necessarily think about user roles and permissions. And in many cases fail to shut the environment down. No fault of theirs – in an on-premise world, dev/test systems were as isolated as they could be. Securing a dev/test environment was and is not part of their normal workflow. This seemingly innocent oversight, as we now know is the open-door invitation for perpetrators.
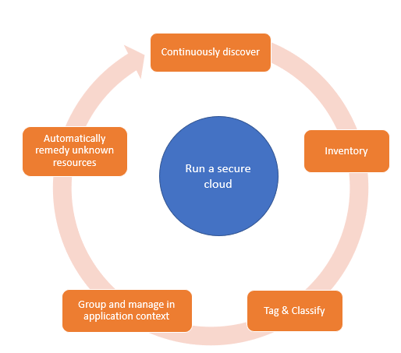
The simplest of AWS applications usually has tens of Amazon EC2 instances, one or more instances of Amazon RDS, Amazon S3, Network Load Balancers, encapsulated into Amazon VPC and are often dynamic. Most customers have hundreds of such applications in two or more accounts, and across two or more regions for redundancy. Modern server-less and containerized workloads can include 100s of resources that are hard to track and manage, Whether you are deploying a new application, or you would like to manage your existing AWS footprint, resource sprawl over time leads to security and cost challenges and results in operation inefficiencies.
Traditional discovery and inventory methods are point in time, expensive and in the cloud become instantaneously outdated. To maintain a robust security and compliance posture, IT teams need an up-to-the-minute view of their environment. The view needs to be comprehensive and include the resources, services as well as all the configurations and permissions. IT teams also need a comprehensive view that spans all their cloud accounts and regions to be effective.
In the case of our pharmaceutical customer, their footprint spanned over sixteen accounts. Instant discovery revealed that over 20% of their resources were either overprovisioned, unmanaged, or even abandoned. This led them to purge the excess and put tight governance controls in place. In the process they also standardized and self-serviced provisioning, such that their application teams were not impacted.
Modern applications are highly interconnected. Changes to a core group of services may impact multiple applications. For example, at our pharmaceutical customer, the web front end, inventory, procurement, fulfillment, and billing are all interconnected. One of the critical pillars to visibility is context. IT teams need to understand first what applications or users are using a resource or a service. Tagging is an effective management strategy. To build an effective security strategy IT teams also need a solution that enforces tagging, understands the tags, builds associations and provides the application, user or departmental context. This context is necessary for policy building, remedial action as well as forensics.
Getting continuous visibility and assessment requires specialized skills. Scaling by hiring experts who can write and maintain code is one option. This is a classic Architect/Expert model. In researching for this blog, I discovered that there are over 100,000 open job positions for security experts, with costs ranging from $150,000/Yr. for security managers to over $300,000/Yr. for senior cloud security architects. Some applications such as real time trading applications may need this level of investment in people.
However, for the vast majority of applications, including Dev/Test, IT teams can automate the discovery, inventory, classification and visualization. An expert/IT operator model is more efficient. Expert cloud security architects to create the guidelines and enable their IT Administrators to automate the process with tools such as MontyCloud DAY2™ Discovery & Classification.
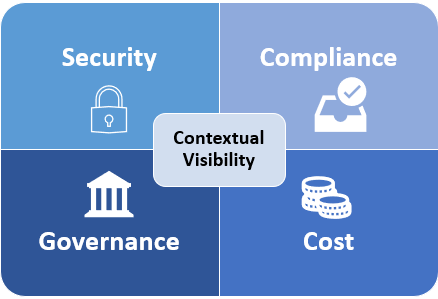
You can only secure and manage what you know is in your domain. By establishing an all-seeing eye with continuous visibility ensures that you can design effective, granular controls for an ever-changing environment spanning security and a number of other management areas such as compliance, governance and cost. Furthermore, solutions like MontyCloud DAY2™ enable you to collect and tag vast amount of information.
In addition to visibility and management, you can also reliably automate reactions and remediations. For example, if one of your applications provisions an Amazon S3 bucket that is exposed to the internet, it is possible that the application inadvertently misconfigured the security control, but it is also possible that it is a customer facing application that needs Internet access.
With the right context, you can automate a quick check and flag, remediate based on policies or allow it. Visibility is the foundational step to a cloud center of excellence.
MontyCloud DAY2™ can automate free security and compliance posture assessments in just five easy steps. Signup for a free MontyCloud DAY2™ account today and immediately:

Have you signed an agreement to begin migrating to AWS? Or are you a Managed Service Provider (MSP) with an AWS Migration Competency delivering AWS...

The Imperative of Infrastructure as Code (IaC) Just as blueprints are vital for constructing resilient physical infrastructure, Infrastructure as...

Today I am super excited to announce the availability of MontyCloud’s CoPilot for Cloud Operations, an interactive Agent for simplifying Cloud...